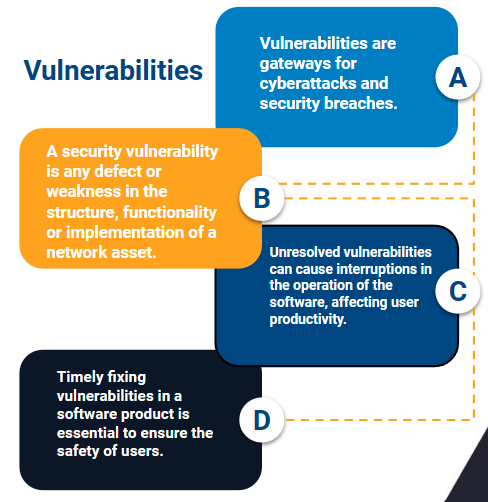
Rechercher les vulnérabilités dans vos bases de données Azure SQL - Microsoft Defender for Cloud | Microsoft Learn
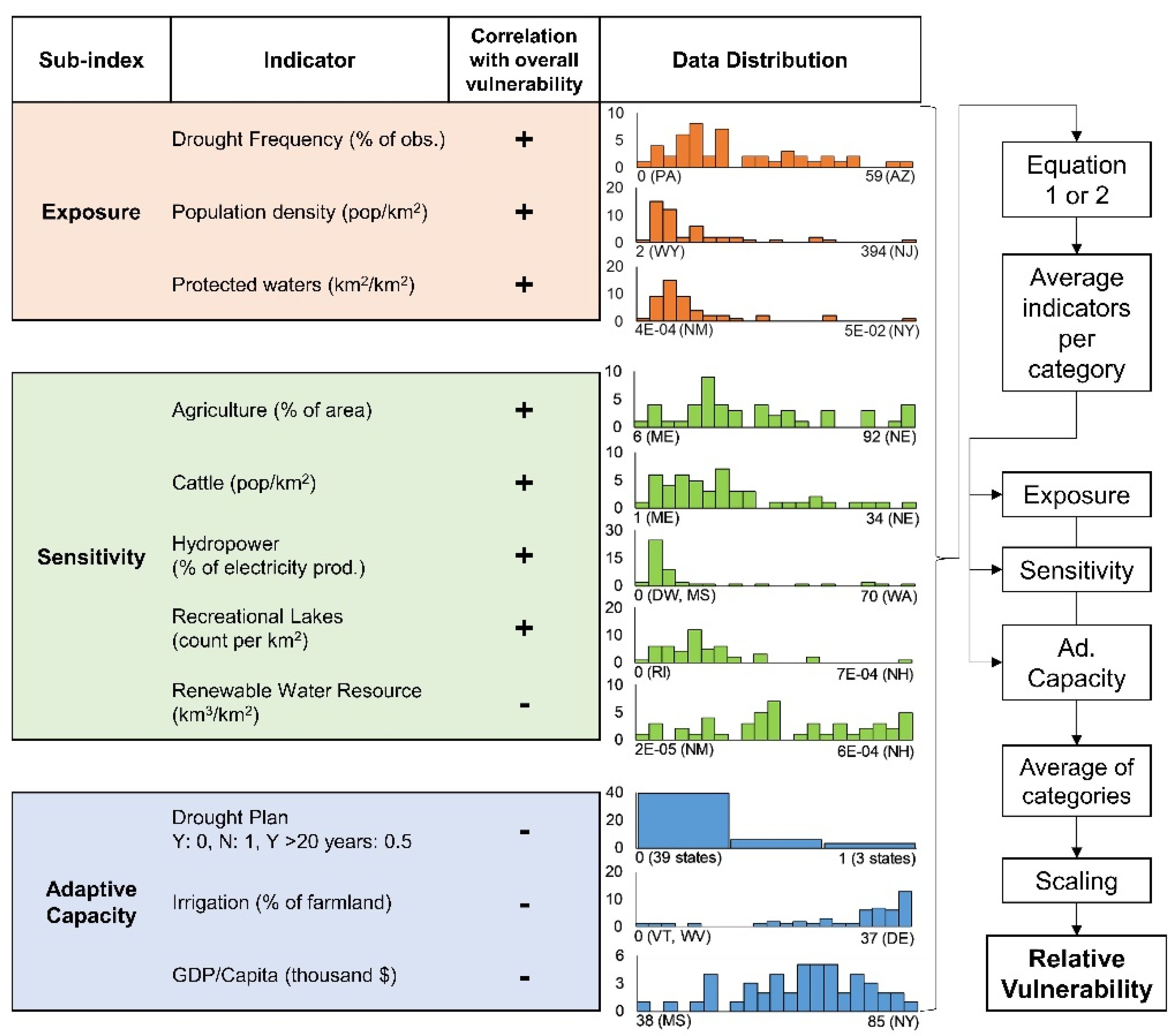
Water | Free Full-Text | Correction: Engström, J., et al. Drought Vulnerability in the United States: An Integrated Assessment. Water 2020, 12, 2033
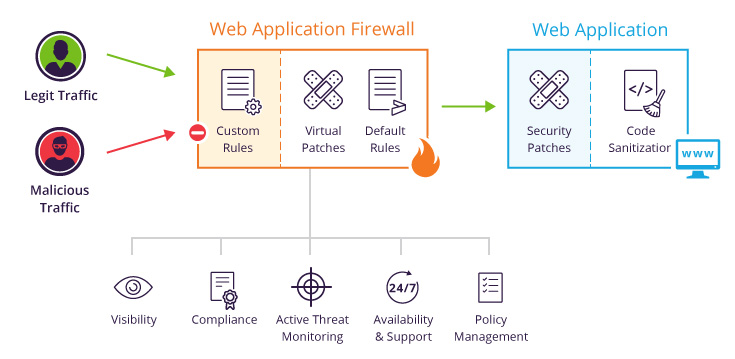
Analyse des vulnérabilités | Outil d'analyse des vulnérabilités - ManageEngine Vulnerability Manager Plus
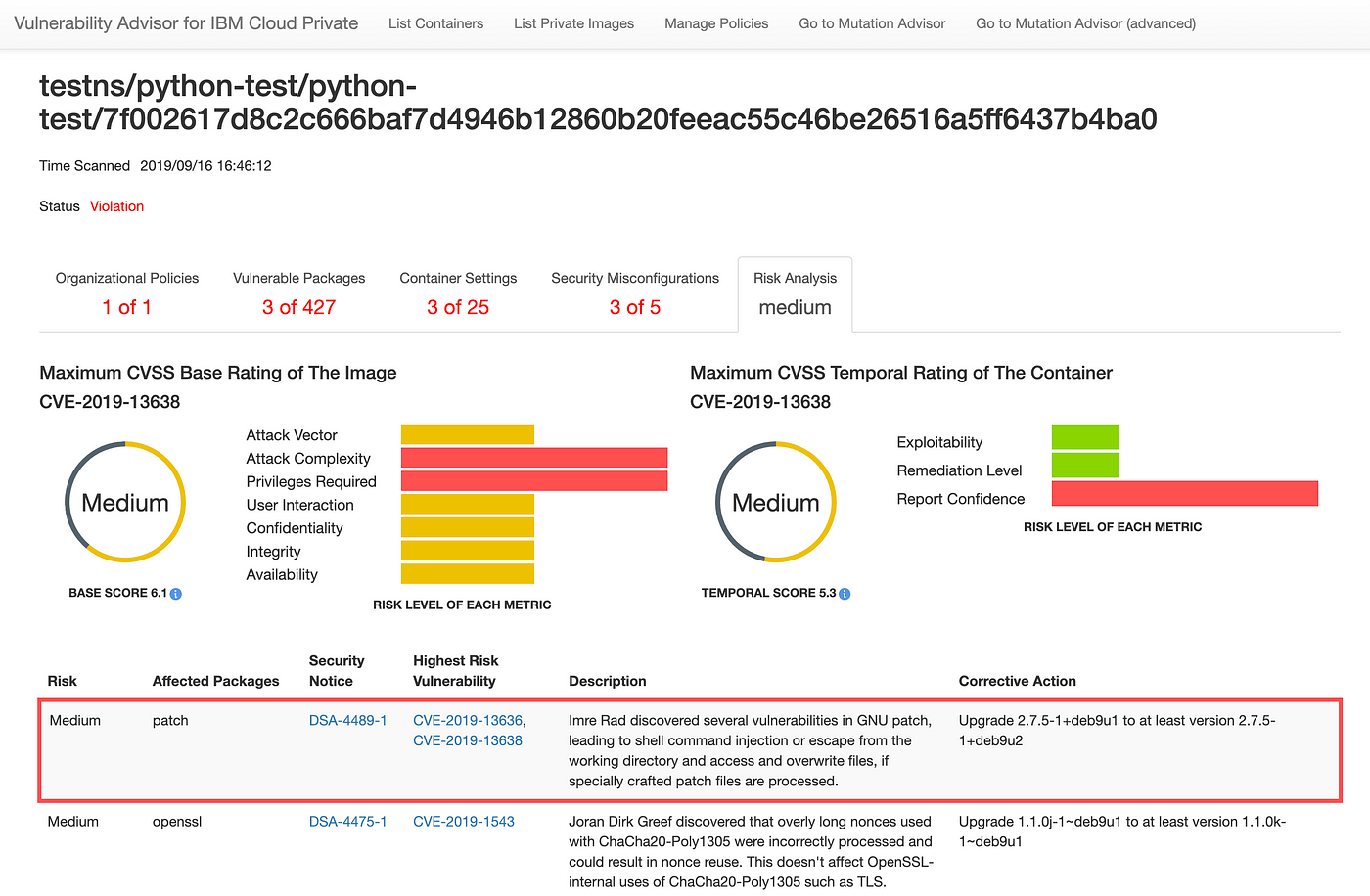
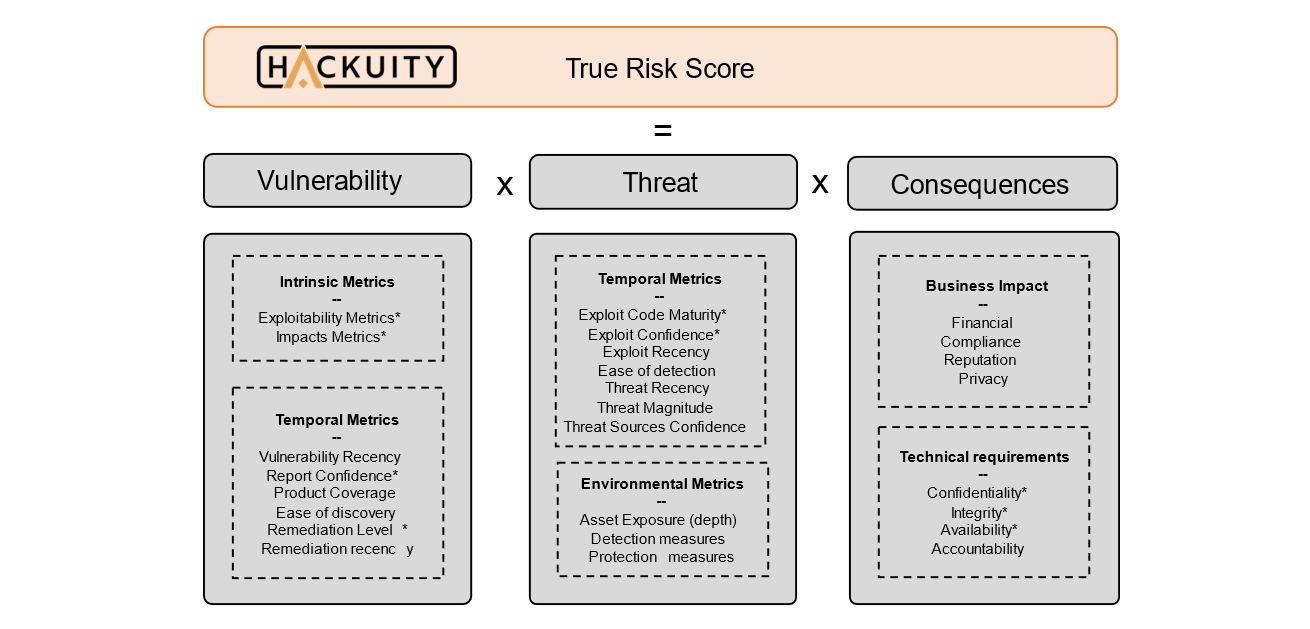
Assessing security risk of your containers with Vulnerability Advisor | by Yuji Watanabe | IBM Cloud | Medium
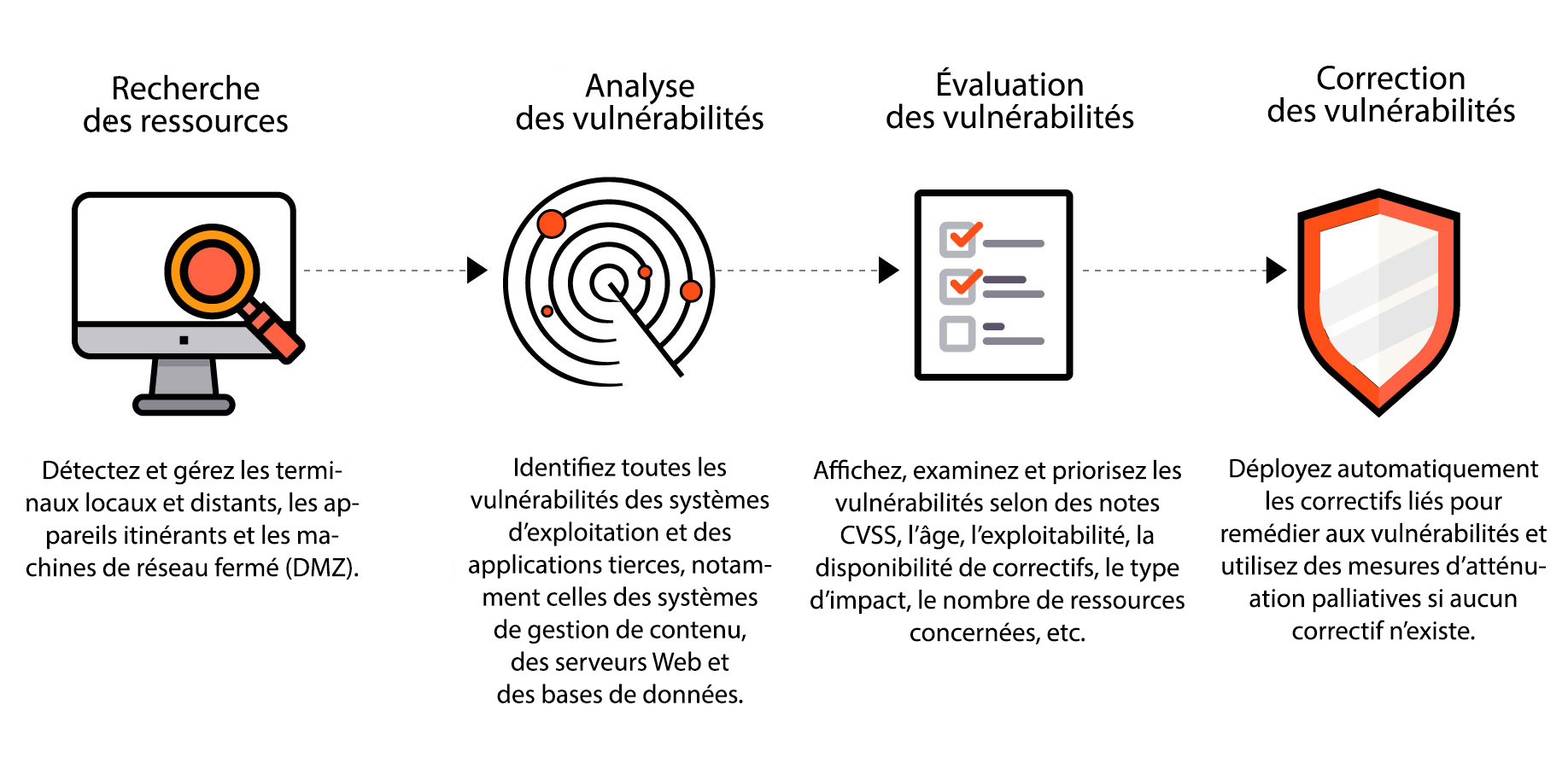
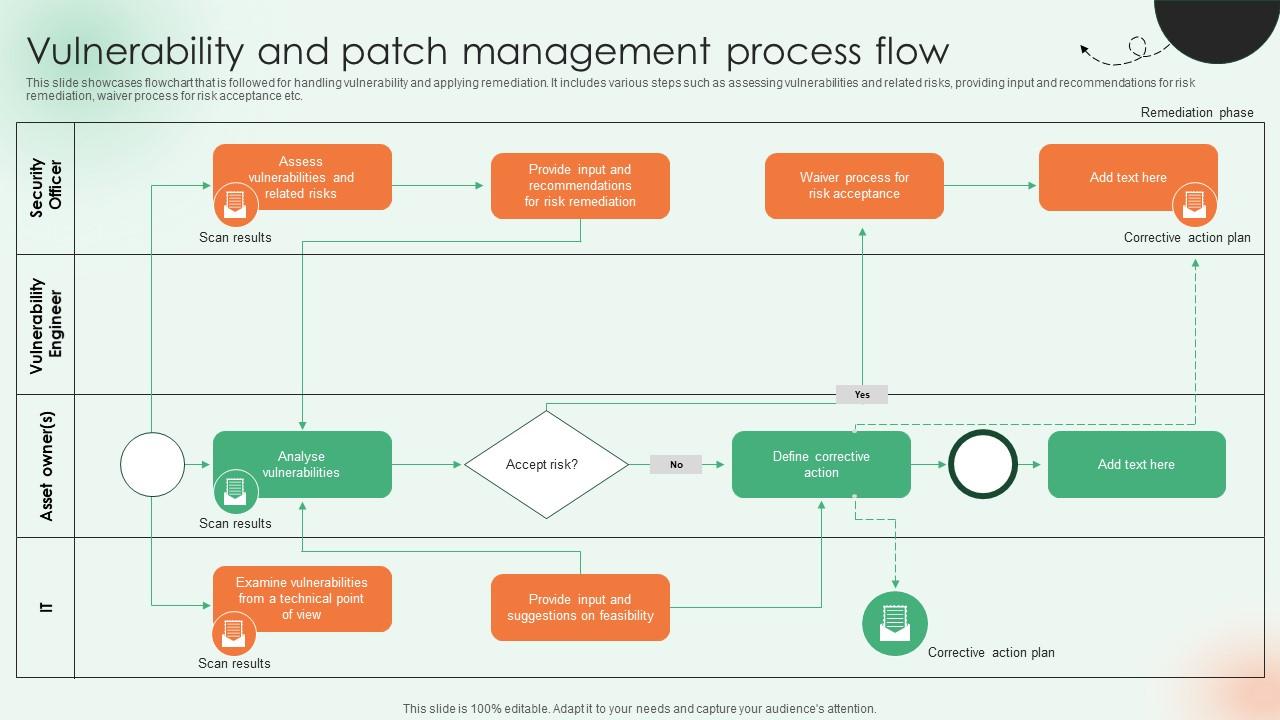
Définition de la gestion des vulnérabilités | Processus de gestion des vulnérabilités - ManageEngine Vulnerability Manager Plus








![Hikvision, HWG Deceive FCC About New Critical Vulnerability [Update: Hikvision Issues Correction] Hikvision, HWG Deceive FCC About New Critical Vulnerability [Update: Hikvision Issues Correction]](https://s.ipvm.com/uploads/793a/1233/f070eec5-c708-4b8f-aa06-104197bc26dd.jpg)